Speed up yourinternal networkpentestingand achieve better results
Manual and automatable pentesting - all in a single, integrated suite, built for internal network pentesters.
Double your efficiency with better quality.
WHY CHOOSE US
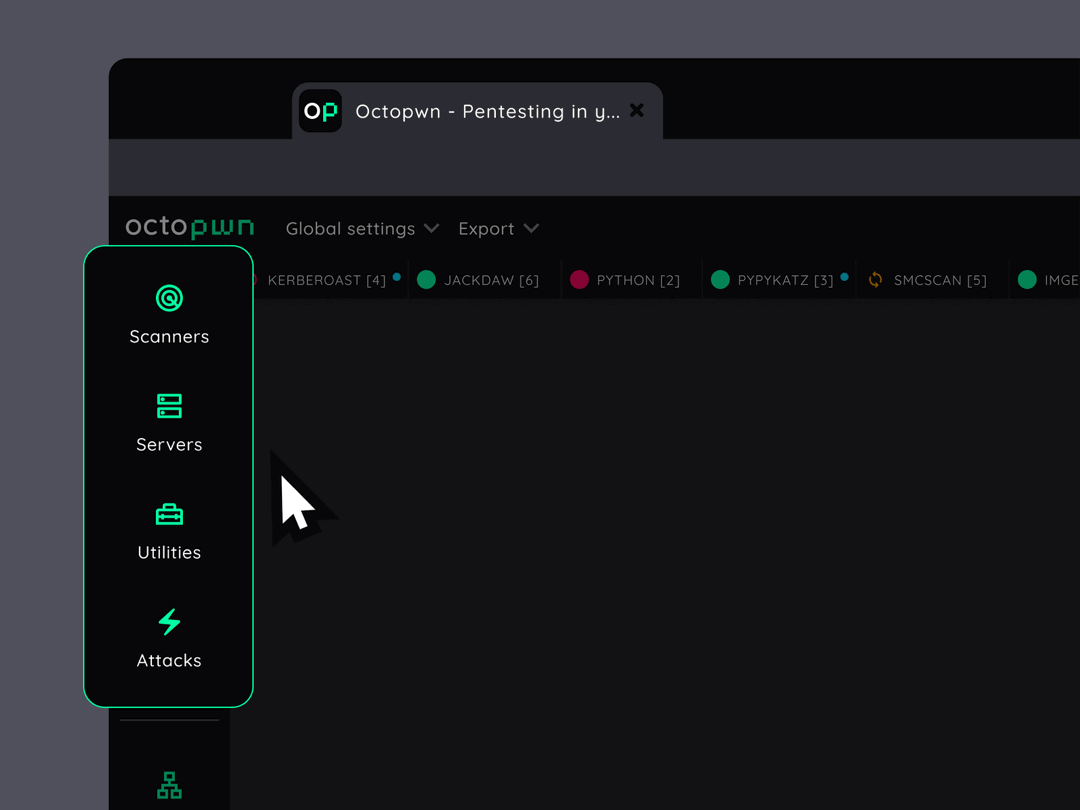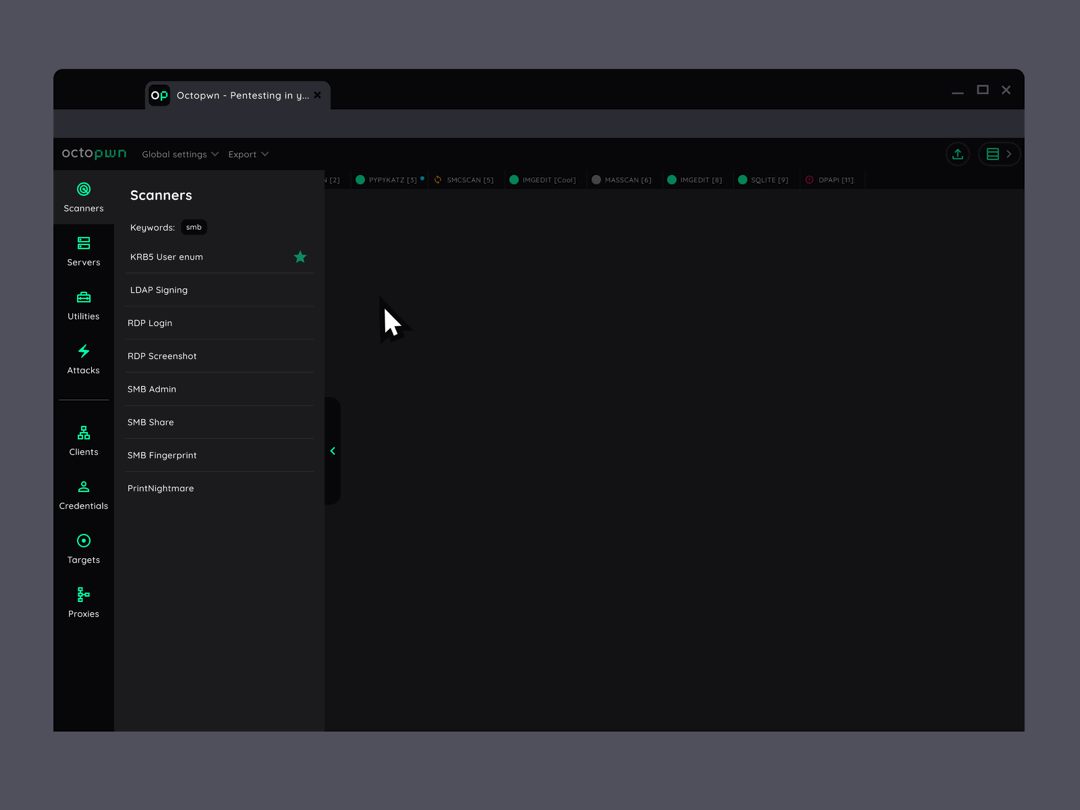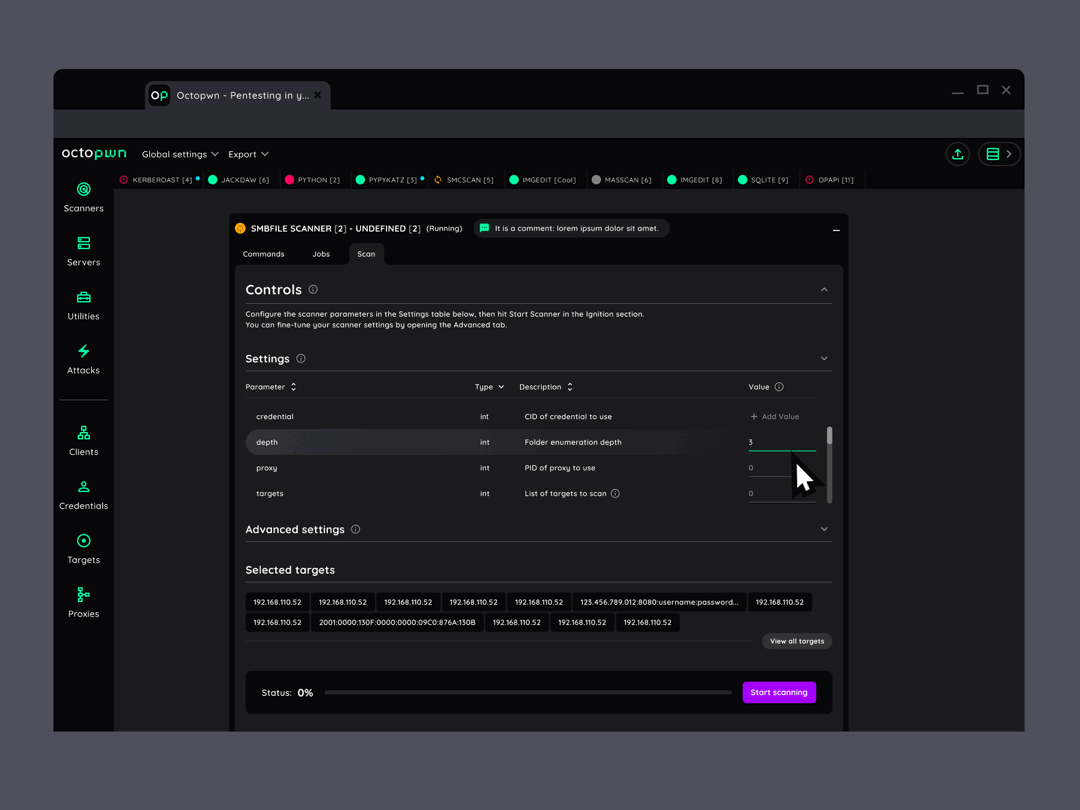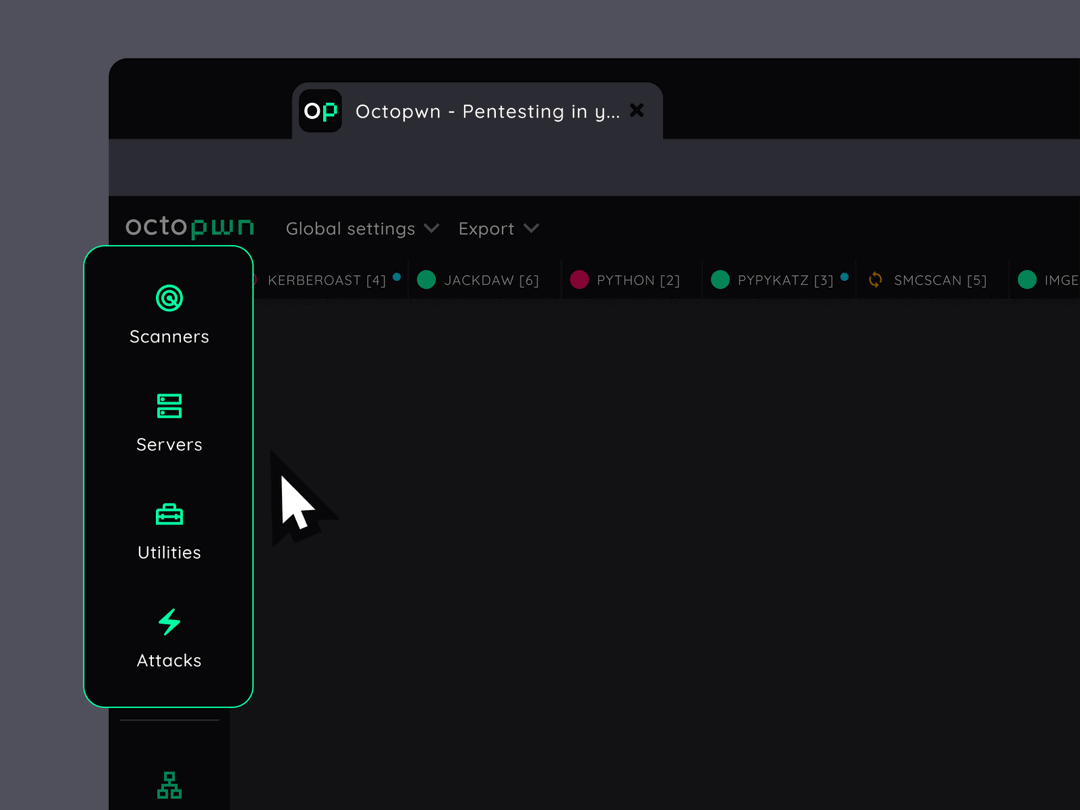
All the tools within one suite
Fully built from scratch by us, all scanners, clients, attacks and other custom utilities are implemented in Python. They run on a unified framework, all bundled on top of Pyodide, running in Webassembly. Inside your browser - no cloud, no backend.
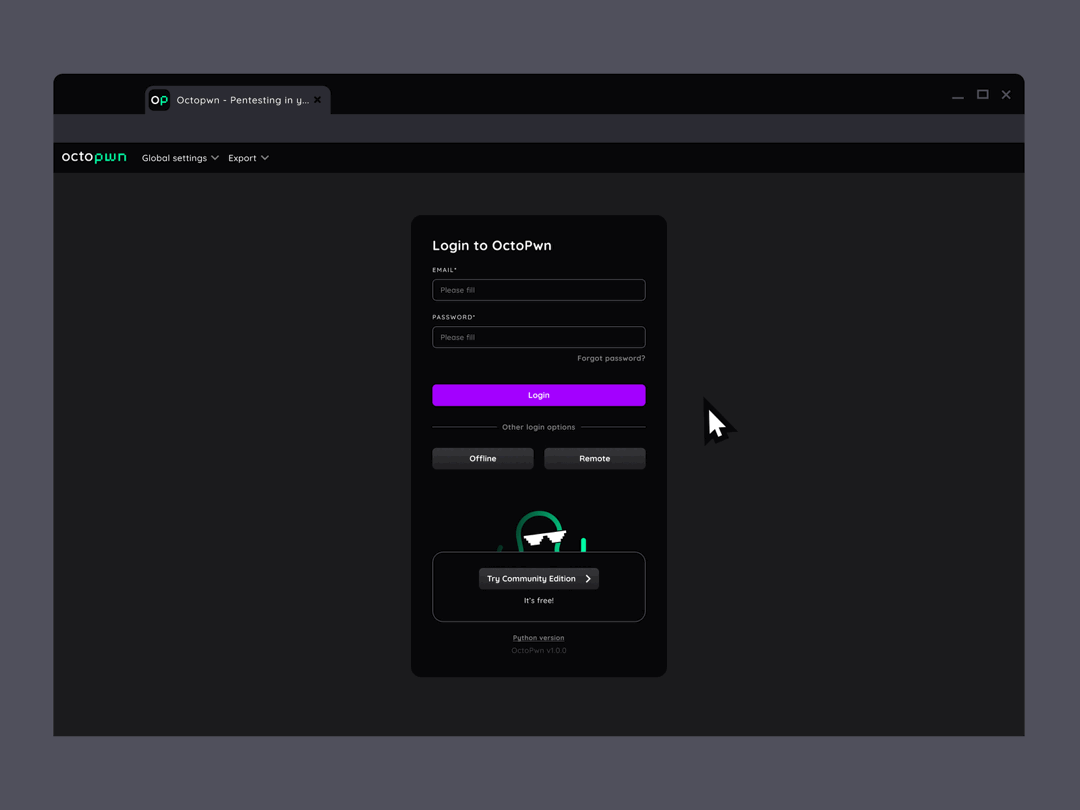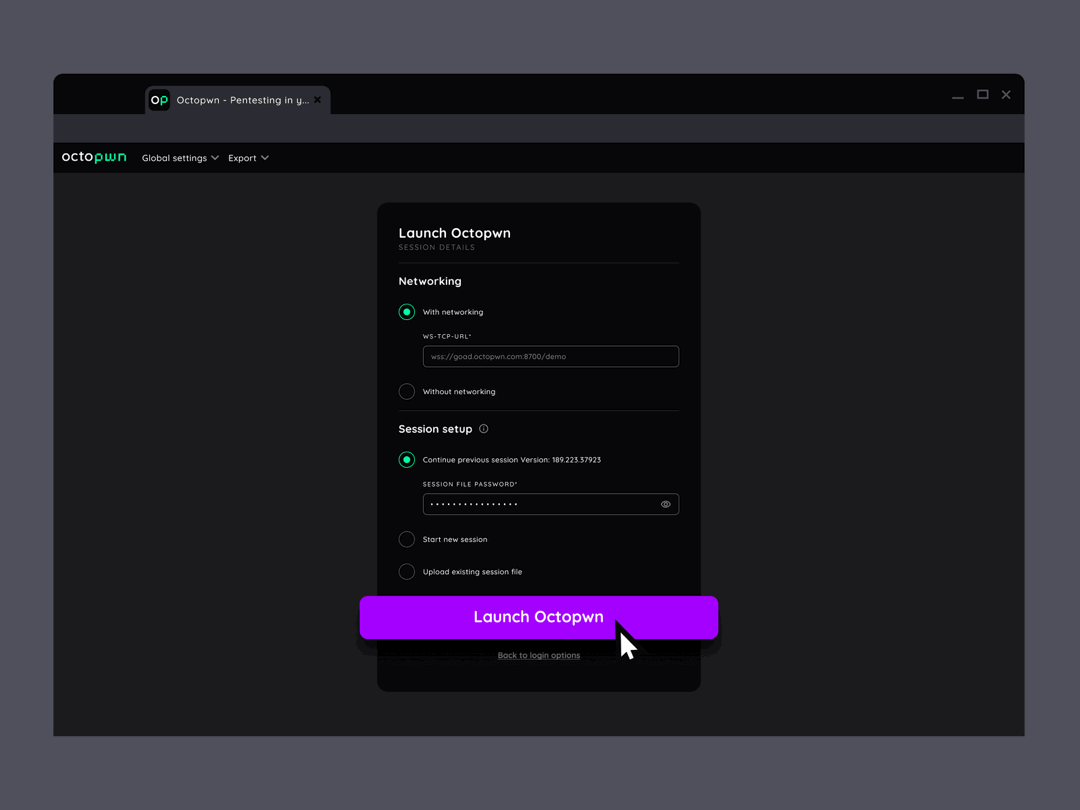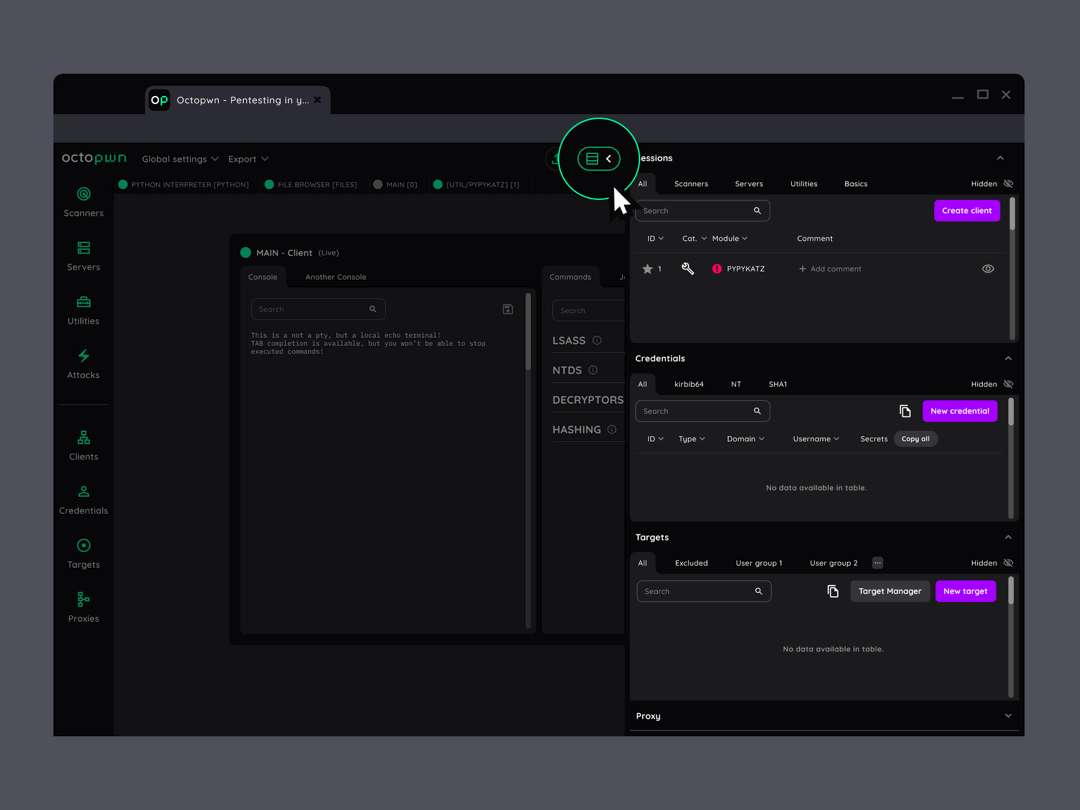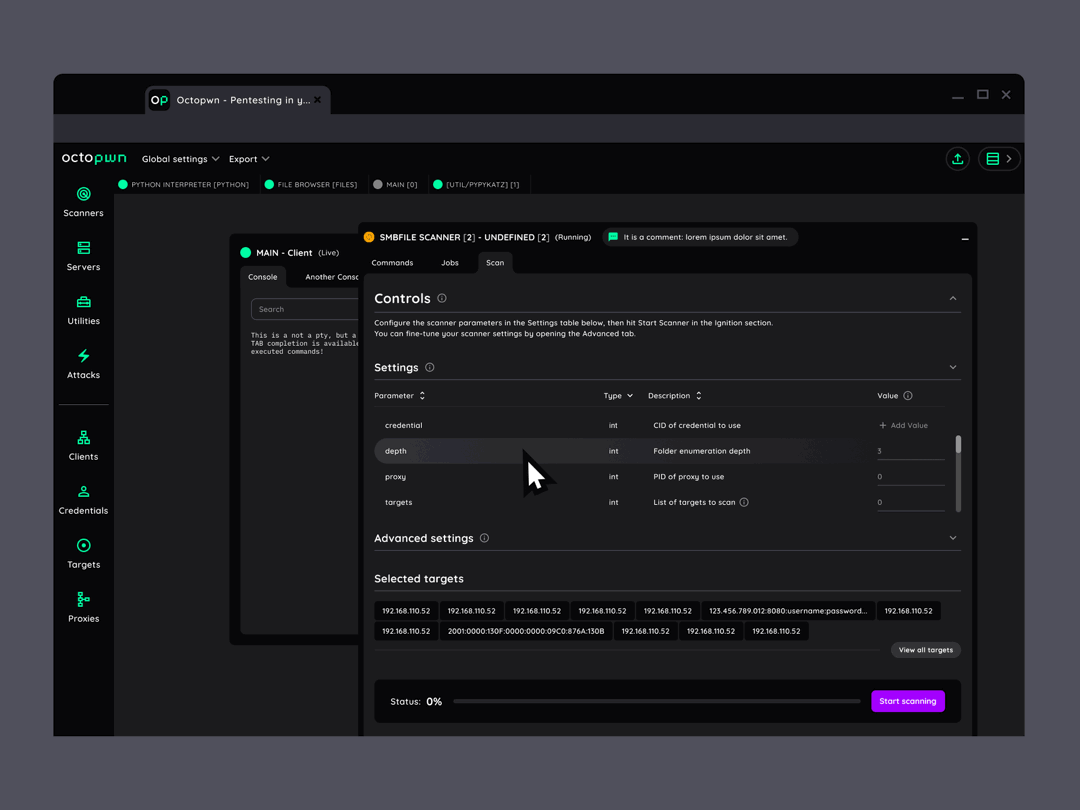
Fast setup and results
No installation needed and only one tool to learn - deploy our proxy application quickly on the target network and start pentesting immediately.
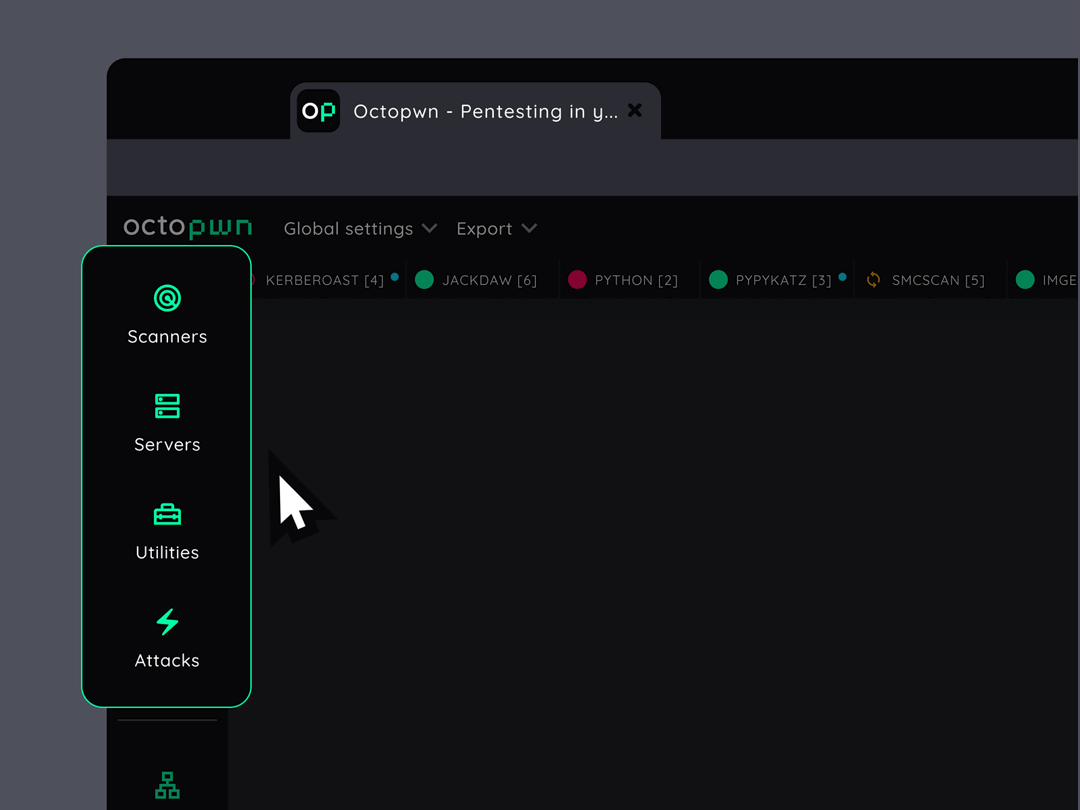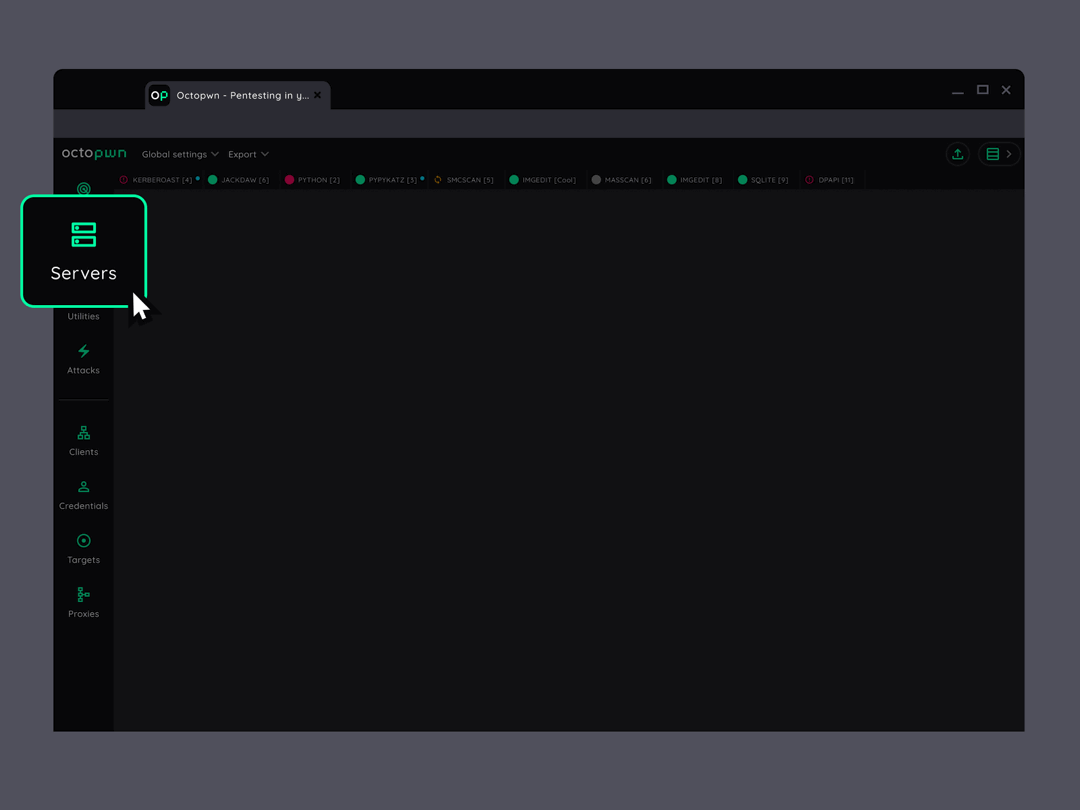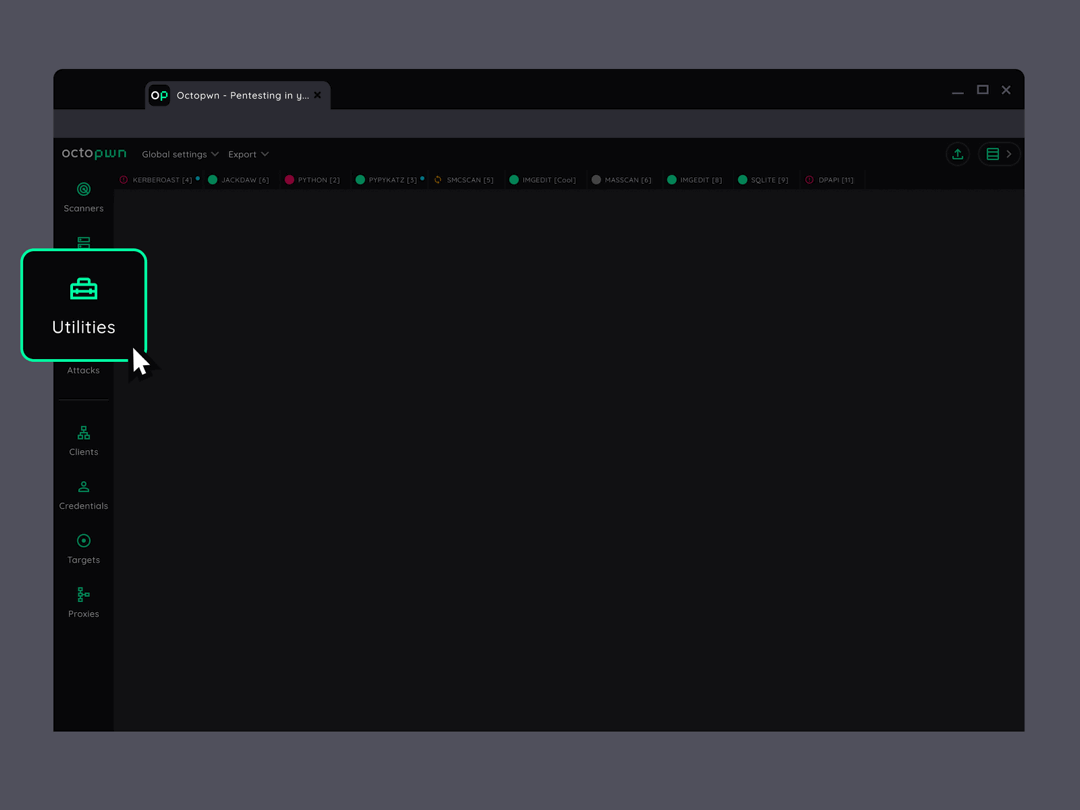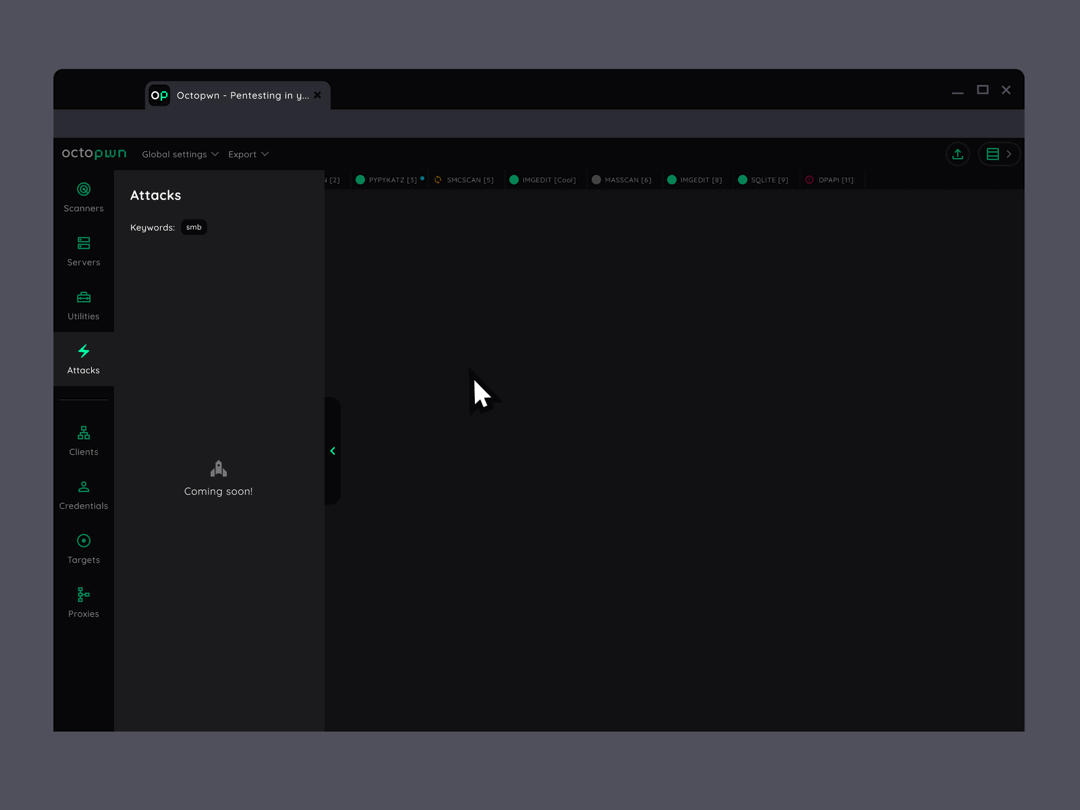
Get your job done under any conditions
All essential scanners, clients, utilities, attacks and proxies are integrated on a single data platform. Hassle free pentesting even in monitored environments.
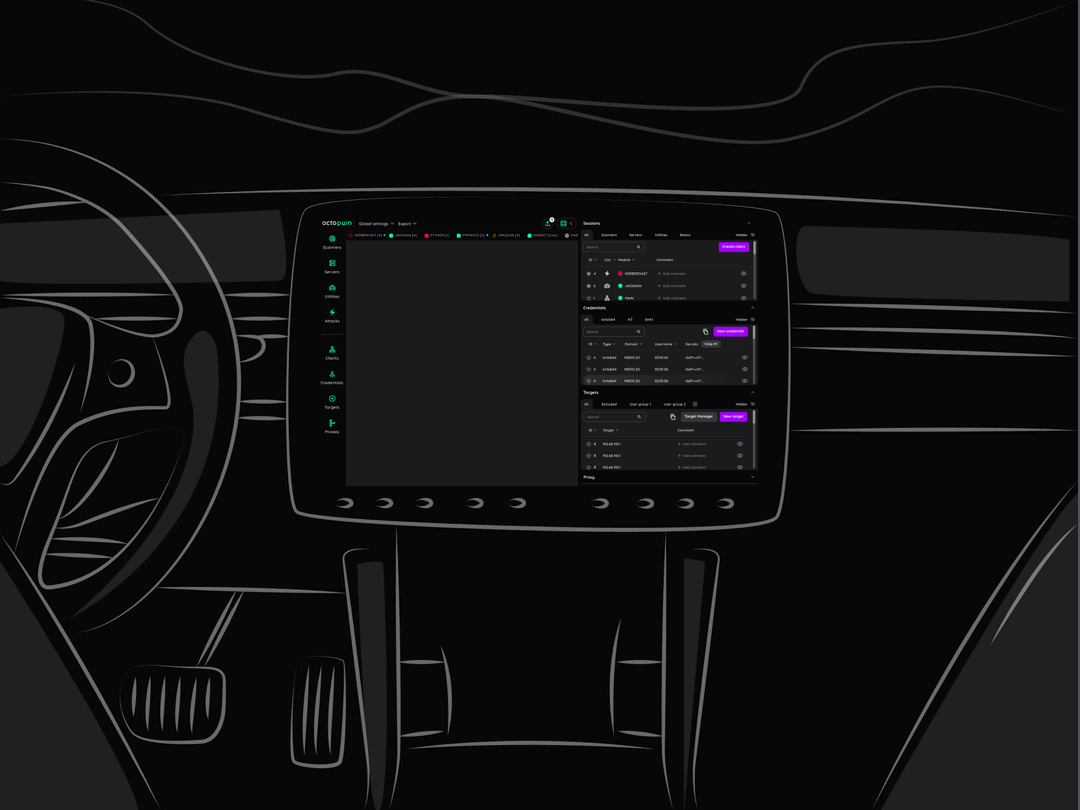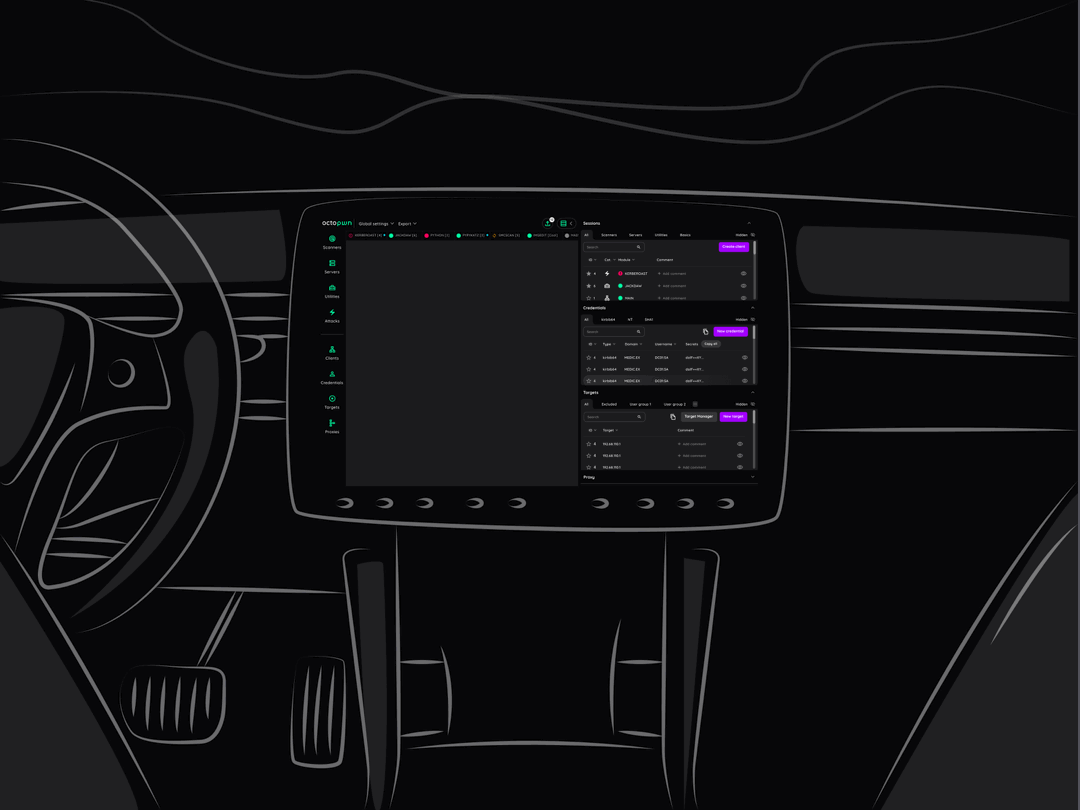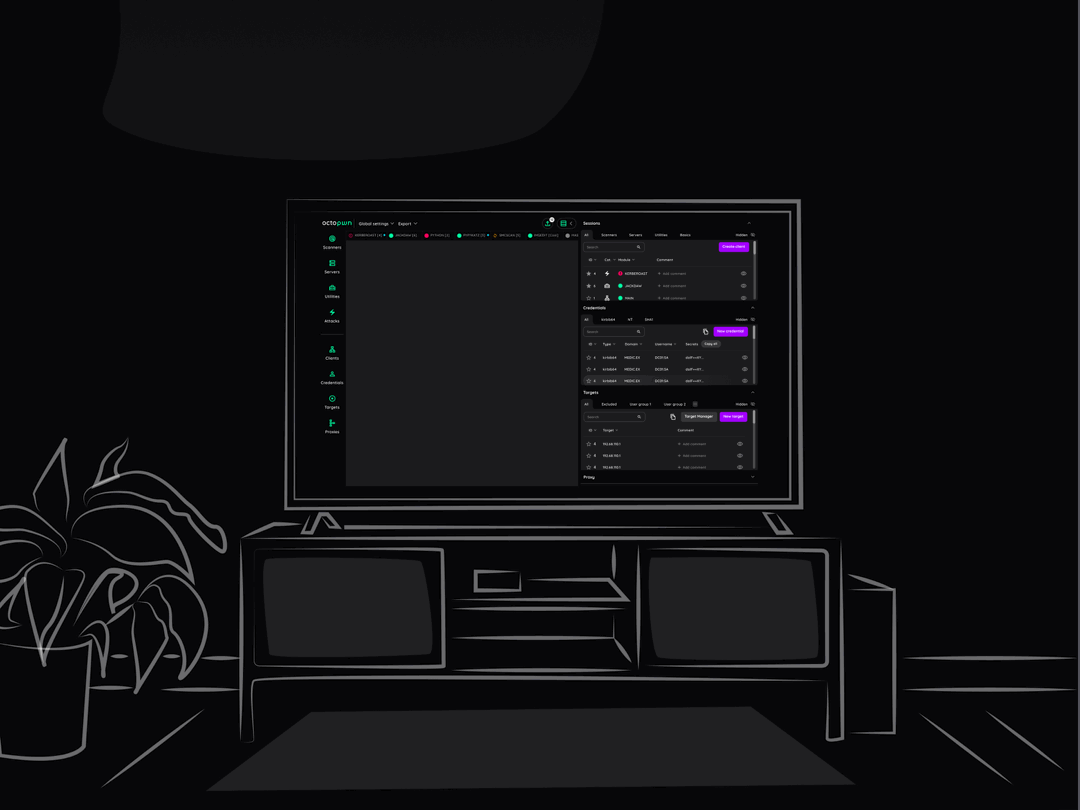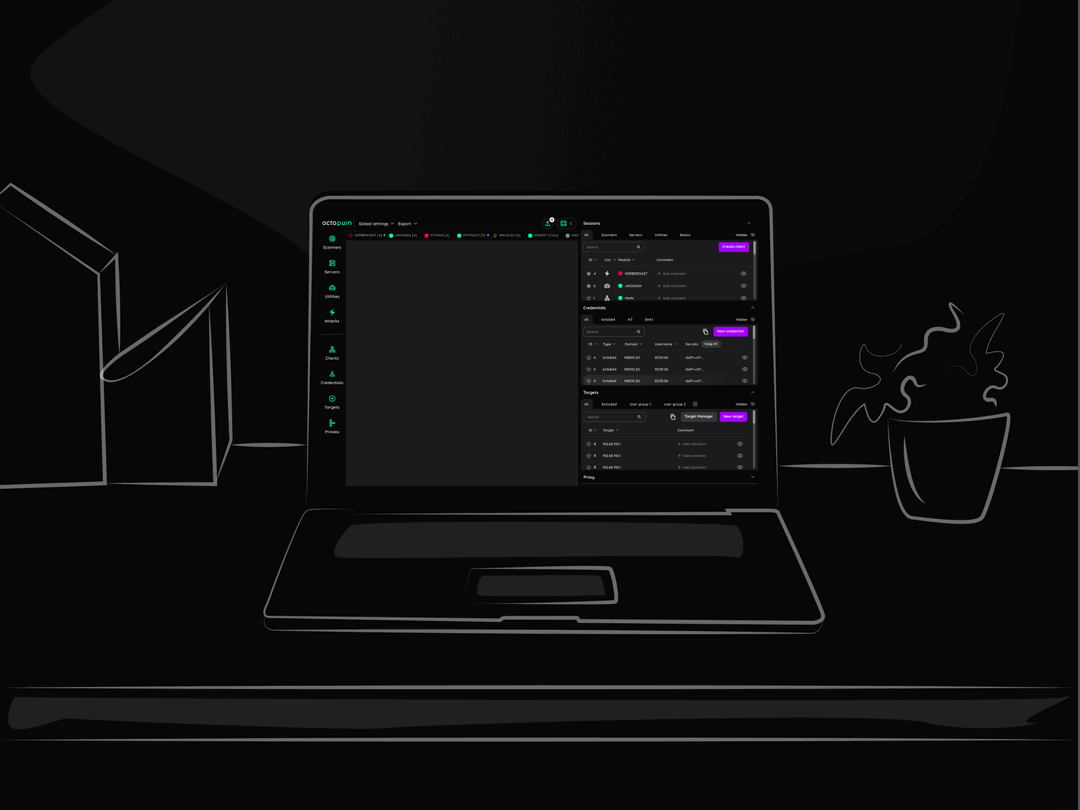
Add your custom tools, automate your workflow
Our API allows you to add your own tools and build custom workflows to speed up your work.
What you can do
Both manual and automated internal networkpentesting to save time and improve quality.
Easy data import and export
Move data in and out easily from nmap, Hashcat, Bloodhound, Masscan etc.
with automatic parsing of credentials, targets and clients.
All data is stored encrypted in your browser
We do not store anything about how you use our product or what projects you do with it.
Your data is always stored encrypted in your browser.
Comprehensive logging for easy reporting
Command / execute time stamping and logging done for you automatically.
Full session save / restore
Continue easily from where you left off.
Deploy remotely through VPN
Our proxy application can be deployed on localhost and on remote systems as well.
Developed in Switzerland.
Pricing
Choose your plan
Community
Free forever
Try now
Pro
recommended
499 €
/ year
Get started
Enterprise
Full automation (Autopwn)
Binary version
Full hashcat, nmap and LLM integrations
Contact us
How you can learn more
Become better at pentesting
Featured video
Hacking from the Browser
Tamas Jos presents OctoPwn in action at Area41.
07/17/2022
Video
Spooky Authentication at a Distance
Tamas Jos Defcon talk on YT! "This project was years in the making and this was a big milestone :) Please, enjoy!"
9/15/2023
Watch Video
Latest article
Weirdness while parsing LSASS minidumps
LSASS encrypts user credentials using AES-CFB which means that most of the secret values can be decrypted using an incorrect IV...
06/01/2022
Read more
Article
Play with katz, get scratched
In this article I’ll show step-by-step how to recover credentials even when paloalto’s Cortex XDR is “actively protecting” LSASS...
11/6/2020
Read more
Made with love in Switzerland. Hack safely, use Octopwn.
All rights reserved. - Octopwn - 2026
ver: hhxl48